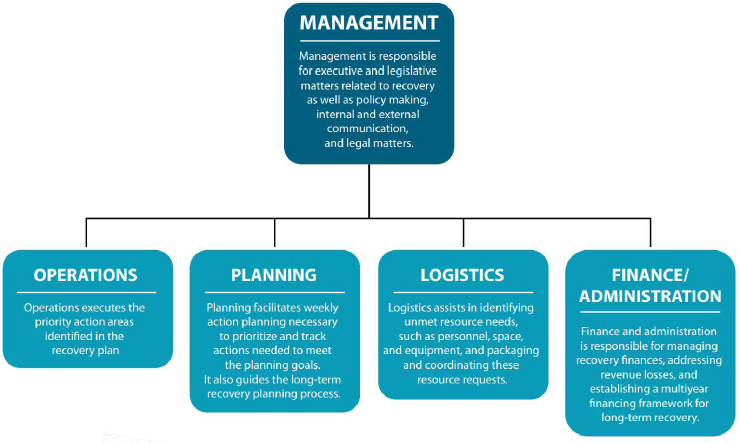
The model helps frame issues related to disaster preparedness as well as economic and business recovery after a disaster. The four phases of disaster.
 Business Continuity Disaster Recovery Business Impact Analysis Rporto
Business Continuity Disaster Recovery Business Impact Analysis Rporto
Follow the disaster recovery plan DRP c.
What is the first step in a disaster recovery effort. Step 1 in disaster recovery planning is to think about the different disasters that could endanger your business. 1 Define all important assets. Respond to the disaster b.
If youre starting to put together your disaster recovery plan or youre looking to improve an existing plan assembling the right DR team is a vital first step. The first critical step in a disaster recovery plan is to ensure that everyone is safe. The second step is responding to the disaster before pursuing recovery and the final step is following the DRP which includes communicating with all affected parties.
Which of the following is a critical first step in disaster recovery and contingency planning. Securing funding and identifying who is involved are critical first steps in a recovery effort. Risks need to be balanced with the goal to expedite recovery.
The first step in creating a comprehensive disaster recovery plan DRP is to document likely impact scenarios. Successful disaster recovery requires practical integration of the recovery plan with the institutions family of plans including the long-range strategic plan the annual capital plan the ongoing facilities master plan the business continuity plan the emergency operations plan and the financial recovery plan. The first step in creating a comprehensive disaster recovery plan DRP is to document likely impact scenarios.
Some common examples are. For a business to be able to recover from an emergency or natural disaster planning is the first step. Develop the continuity planning policy statement.
Power outages which can cause network failures and important equipment breakdown. What are the steps to create a Disaster Recovery Plan for your business. Electrical fires broken water pipes and floods.
Complete a business impact analysis. Your organization has several important assets but to create a DR plan you first need to define what assets are of utmost importance to keep your business running. The correct disaster recovery steps and their associated definition mappings are laid out as followsi.
It is designed as a working guide that will direct you through the steps as you consider how to proceed post-disaster as well as how to prepare for a possible threat or natural disaster. Ensure that everyone is safe. Building infrastructure problems eg.
Communicate with all affected parties d. Without the proper personnel working together collaborative DR planning can be disjointed and incomplete. It is only after.
Organizational ramp-up fund management and close monitoring of procurement and bidding will be essential to mitigating fraud waste and abuse. Creating a DR plan is an important aspect of your BCDR strategy. Determine offsite backup facility alternatives.
Accompanying a community through all the phases of disaster recovery requires a long-term commitment by The United Methodist Church. Write a policy that provides the guidance necessary to develop a BCP and that assigns authority to the necessary roles to carry out these tasksii. Plan testing and drills.
What is the first step in a disaster recovery effort. Organize and create relevant documentation.


